There’s a new file-encrypting Bitcoin ransomware on the loose called CTB Locker (Curve-To-Bitcoin Locker, or Critroni), and it’s using Tor to transmit data and remain anonymous. Experts say it’s one of the most advanced they’ve ever seen and it’s targeting computers running Windows XP, Vista, 7, and 8. You won’t likely know that you’ve been infected until your files are already encrypted.
According to a Kaspersky blog post written by senior malware analyst Fedor Sinitsyn:
“By using TOR, criminals make it harder to trace their activity and seize malware control servers. Using Bitcoins, an anonymous cryptocurrency, as the exclusive payment option, makes following the money complex too. What does it mean for ordinary users? Criminals will likely be able to use this malware for a long time. In addition, the malware is being sold on underground forums and attracted international attention. That’s why we expect further infections in other regions, especially in the U.S., UK and others, that have proven to be good “markets” for ransomware.”
While it’s similar in function to CryptoLocker (which was recently shutdown through intergovernmental efforts), CTB Locker is said to be run by a different group, using extremely advanced new technology known as elliptical curve cryptography. The malware communicates with its control server through Tor instead of the regular internet, making it even more difficult for law enforcement to track, as done with CryptoLocker.
CTB Locker is detected by Kaspersky as Trojan-Ransom.Win32.Onion, and is distributed by the Andromeda botnet and a malicious worm of the Joleee family, which downloads and executes the CTB Locker ransomware. The malware is being distributed through web pages with exploit kits designed to initiate downloads to a victim’s computer.
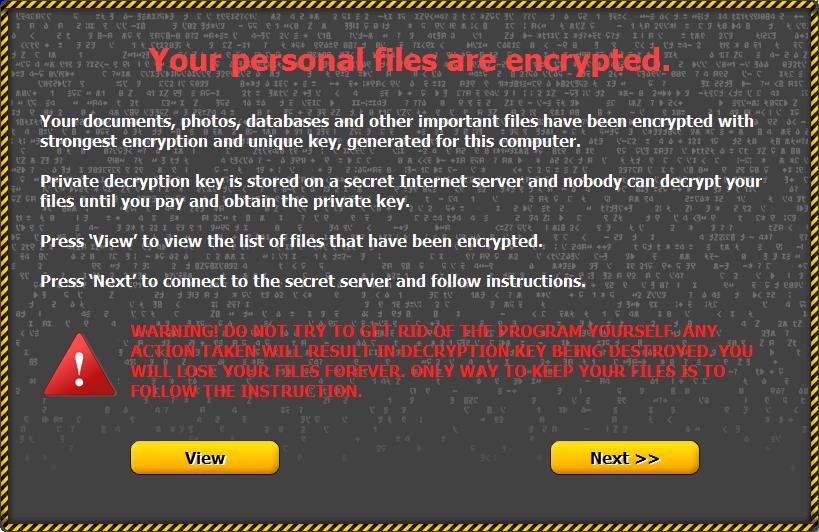
Once infected with CTB Locker, the malware scans your computer for important documents, photos, databases and other files, moves and compresses the files in a temporary file, then encrypts them with unbreakable Elliptic Curve Diffie-Hellman cryptography.
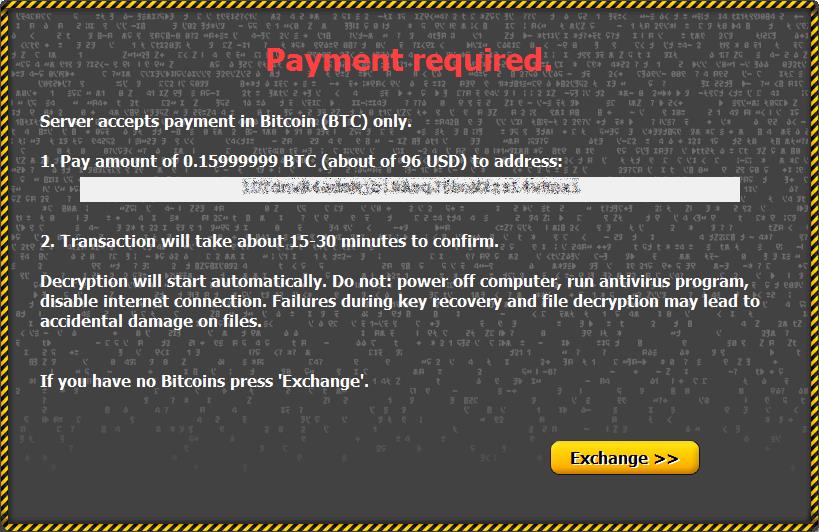
A window is then displayed informing you that your files have been encrypted and that you need to pay a ransom between 0.2 and 0.5 bitcoins to recover them. The ransom must be met within 72 hours or you risk having files permanently locked. The ransomware programmers were kind enough to program it to set your desktop background to an image with instructions on how to pay the ransom and recover files.
Once the ransom is paid, a key is sent that can be used to decrypt your files, but not enough data is out there to determine if the cybercriminals actually hold up their end of the deal and allow you to decrypt your files.
One aspect of the CTB Locker malware that makes it so unique is that it communicates with its command and control server over the Tor network without the victim having Tor installed. CTB Locker programmers were able to implement part of Tor’s open source code into their malware, allowing it to communicate without the Tor Browser Bundle actually being installed.
“All the code needed to implement interaction with the anonymity network is statically linked to the malicious program’s executable file (i.e., is implemented as part of the malicious code) and is launched in a separate thread,” said Sinitsyn.
The cybercriminals even set up their own .onion site to handle ransoms.
Sinitsyn continued:
The sample analyzed has a single static command server address, which belongs to the .onion domain zone.
It is worth noting that this in itself is not ‘innovative’. We have seen similar arrangements in other malware types (discussed, for example, here and here).
However, this is a new development for ransomware. Although some of the ransom Trojans from families detected earlier demanded that the victim visit a certain site on the Tor network, the malware discussed here supports full interaction with Tor without the victim’s input, setting it apart from the others.
There unfortunately appear to be few recovery options at this time. In a detailed guide on how to best protect yourself from CTB Locker, BleepingComputer.com writes, “the only methods you have of restoring your files is from a backup, file recovery tools, or if your lucky from Shadow Volume Copies.” Another removal guide can be found here on the VilmaTech blog.
According to BleepingComputer, this particular malware is also being sold online for $3,000 USD as part of a hacking kit, which even includes support to help get the malware up and running.
According to BleepingComputer, the following method can be used to prevent CTB Locker from infecting your computer:
You can use the Windows Group or Local Policy Editor to create Software Restriction Policies that block executables from running when they are located in specific paths. For more information on how to configure Software Restriction Policies, please see these articles from MS:
http://support.microsoft.com/kb/310791
http://technet.microsoft.com/en-us/library/cc786941(v=ws.10).aspx
The file paths that have been used by this infection, and others, are:
C:\.exe
C:Users\AppDataLocal.exe (Vista/7/8)
C:Users\AppDataLocal.exe (Vista/7/8)
C:Documents and Settings\Application Data.exe (XP)
C:Documents and Settings\Local Application Data.exe (XP)
%Temp%
In order to block the CTB Locker you want to create Path Rules so that they are not allowed to execute. To create these Software Restriction Policies, you can either use the CryptoPrevent tool or add the policies manually. Both methods are described below.