The U.S. Justice Department announced earlier this week the success of the multi-national effort to disrupt and disable two of the most malicious malware programs in existence, GameOver Zeus and Cryptolocker, which was done by secretly seizing control of two computer networks used by the people responsible for the software.
One of the programs, GameOver Zeus, is a global botnet – the most sophisticated that the FBI has ever attempted to disrupt – that steals banking information from infected computers through the use of a keylogger, and has stolen millions from businesses and consumers.
Once computers are infected, “they secretly become part of a global network of compromised computers known as a botnet, a powerful online tool that cyber criminals can use for numerous criminal purposes.”
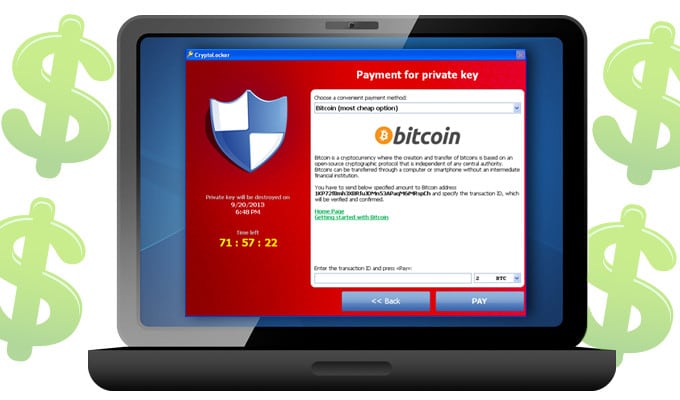
The other, Cryptolocker, is a ransomware program that encrypts infected hard drives and demands payment in bitcoin before access to files is restored. It’s estimated to have infected, as of April 2014, more than 234,000 computers and to have generated more than $27 million in ransom payments in just the first two months of its time in cyberspace.
Both programs were commonly spread through spam e-mail attachments, with the GameOver Zeus network often being used to distribute Cryptolocker. Cryptolocker usually came in the form of spam e-mail attachments disguised as fake tracking notices from FedEx and U.P.S.
Security researchers estimate that the two malicious programs have infected between 500,000 and a million computers worldwide, and according to the FBI, have cost more than $100 million in losses.
Because GameOver Zeus functioned in a decentralized manner, it was the most difficult to shut down. The FBI decided that the best way to gain control over the network was to seize all the servers transmitting the malicious code and to then reroute the traffic to safe computers inside of the U.S..
“These schemes were highly sophisticated and immensely lucrative, and the cyber criminals did not make them easy to reach or disrupt,” said Assistant Attorney General Leslie R. Caldwell.
“But under the leadership of the Justice Department, U.S. law enforcement, foreign partners in more than 10 different countries, and numerous private sector partners joined together to disrupt both these schemes. Through these court-authorized operations, we have started to repair the damage the cyber criminals have caused over the past few years, we are helping victims regain control of their own computers, and we are protecting future potential victims from attack.”
The FBI also released the name of the man they believe to be the leader of the global computer crime syndicate responsible for the attacks, who has now been placed on their list of most-wanted cyber criminals, along with a warrant for his arrest.
The Russian national, 30-year-old Evgeniy Mikhailovitch Bogachev, whose current whereabouts are unknown, was identified as the leader of the group. A 14-count indictment shows that he is being charged with “conspiracy, computer hacking, wire fraud, bank fraud, and money laundering in connection with his alleged role as an administrator of the GameOver Zeus botnet.”
“Bogachev was also charged by criminal complaint in Omaha with conspiracy to commit bank fraud related to his alleged involvement in the operation of a prior variant of Zeus malware known as Jabber Zeus.”
Express.co.uk reported that cyber criminals are now exploiting fear surrounding the Cryptolocker and GameOver Zeus news by sending out e-mails offering a fake fix which secretly installs another virus.
“A spam e-mail has been sent to Windows users that claims to offer decryption keys for the malware which has emptied millions from bank accounts worldwide,” said Express.
“The campaign by hackers claims to unlock any personal files on a PC that have been locked but then downloads onto a computer a dangerous virus.”







